Capture the Flag (CTF) events are hands-on cybersecurity exercises where participants are challenged to identify and exploit vulnerabilities in simulated environments. Unlike traditional training, a CTF places participants in the attacker’s seat, helping them understand how systems are breached and what defensive practices are needed to prevent real-world incidents.
For enterprises, CTFs deliver tangible benefits:
- Improved security awareness across engineering and IT teams
- Exposure to common attack vectors in controlled settings
- Team-building through collaborative problem-solving
- Insights into weaknesses that may exist within internal practices
Contents
How a TrackIt CTF Event is Organized
TrackIt designs and facilitates tailored CTF events, delivered on-site but run against a private cloud-based platform. Each event follows a structured flow:
- Kickoff Briefing: Introducing the event, rules, and objectives.
- Live Hacking Session: Participants exploit vulnerable assets in the sandbox environment.
- Debrief & Retrospective: Review of vulnerabilities, remediation strategies, and best practices.
Events can run from 2–3 hours for software teams to 5–6 hours for security-focused groups. Competitive modes with scoring and prizes are also available.
Challenge Types
TrackIt’s CTF events offer hands-on, practical exposure to a wide range of enterprise technologies and attack scenarios. The challenges are tailored to reflect real-world systems, giving participants a realistic environment to sharpen their skills from both attack and defense perspectives. Challenges span across multiple domains:
- AWS Cloud Environments: Participants engage directly with services including EC2, S3, RDS, IAM, API Gateway, EKS, FSx, and more, facing scenarios such as privilege escalation, misconfigured storage, insecure APIs, container vulnerabilities, and data exfiltration.
- Windows Systems: Exercises often focus on Active Directory exploitation, credential harvesting, and privilege escalation in enterprise-style Windows environments.
- Linux Systems: Challenges include enumeration, service exploitation, lateral movement, and privilege escalation on hardened Linux machines.
- Forensics: Participants analyze compromised environments, logs, and binaries to trace attacker activity, reconstruct timelines, and extract indicators of compromise.
Customizable Events
A key advantage of TrackIt’s CTF is the customizability of challenge levels based on participants’ expertise:
- For Software Engineers (Introductory Level): Challenges are designed to be accessible and require only lightweight tools such as Nmap and the browser inspector. The goal is to help participants grasp the fundamentals of scanning, probing, and identifying vulnerabilities without needing deep security expertise.
- For Security Engineers (Advanced Level): Challenges are more complex and require specialized tools, including Nmap, Burp Suite, Postman, Subfinder, AWS CLI, boto3, Scout Suite, Trufflehog, strings, and others. Participants apply advanced penetration testing techniques, exploit chain building, and cloud security analysis in a controlled environment.
How Vulnerabilities Are Exploited
CTF challenges cover a wide spectrum of attack types and misconfigurations commonly encountered in enterprise environments. Examples include:
- SQL Injection: Exploiting unsanitized database queries
- SSRF (Server Side Request Forgery): Gaining access to internal resources via manipulated requests
- XXE (XML External Entity Injection): Extracting data through insecure XML parsing
- Privilege Escalation: Elevating access from a standard user to administrative control
- Misconfigured IAM or Policies: Abusing excessive permissions for unauthorized access
- Insecure Data Exposure: Exploiting weak data storage or transfer mechanisms:
- Misconfigured S3 buckets that unintentionally allow public access
- Unencrypted database backups or snapshots (e.g., RDS, DynamoDB) exposed to unauthorized users
- Overly broad access controls (IAM policies, role assumptions) granting unnecessary access to sensitive assets
- Media-specific transfer points like open Aspera watchfolders or poorly secured FTP servers
- Misconfigured S3 buckets that unintentionally allow public access
Each challenge mirrors real-world risks while staying fully contained in a secure environment.
CTF Event Delivery Specifics
- The Platform: The event runs on ctf.trackit.io, TrackIt’s private, purpose-built platform designed to simulate realistic attack surfaces in a secure environment. It provides the infrastructure, scenarios, and tracking needed to deliver an engaging and controlled hacking experience.
- Participant Onboarding: All participants are invited through email and can join the event directly without installing any additional software. This frictionless process allows teams to focus on the challenges themselves rather than technical setup.
- Customizable Scenarios: Each event is adapted to reflect the client’s own technology stack, whether it involves AWS services, containerized applications, databases, or operating systems. This ensures that the vulnerabilities explored are directly relevant to the participants’ day-to-day environments.
- Flexible Formats: The CTF can be organized as a competitive exercise with scoring and prizes or as a collaborative session where teams work together. This flexibility makes it equally suitable for team-building, internal training, or focused security workshops.
- Educational Retrospective: Once the challenges are completed, TrackIt provides a detailed debrief. The platform integrates with AWS-native monitoring tools such as GuardDuty, CloudWatch, and VPC Flow Logs, ensuring participants see both the offensive and defensive perspectives. Each session concludes with step-by-step remediation strategies that are practical, field-tested, and directly applicable to real-world production environments.
Strasbourg Capture the Flag Event
TrackIt recently organized a short-format CTF in Strasbourg, France, designed for students and junior software engineers. The objective was to introduce participants to the basics of ethical hacking, demonstrate how real exploitation techniques are carried out, and highlight the importance of secure coding and proper configuration practices.
The event was built on a stack that included AWS resources and common web application components, providing a realistic playground for both reconnaissance and exploitation.
Vulnerabilities Explored
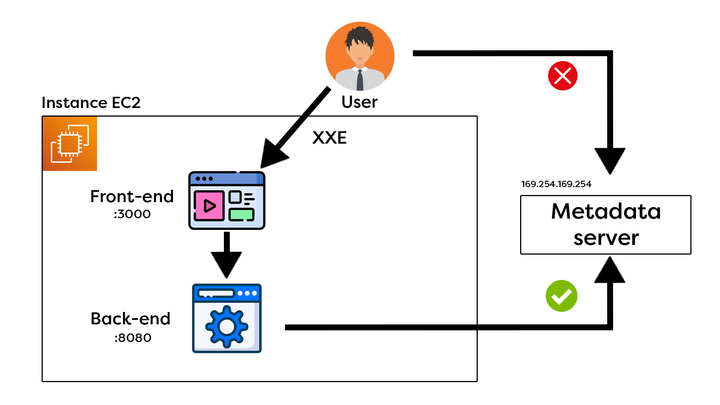
Participants were guided through a series of challenges that reflected common security flaws. They began with a basic Nmap scan to perform network reconnaissance, identifying open ports and potential attack vectors. The session then moved to SQL injection, where unvalidated input could be manipulated to expose or compromise data. Another challenge highlighted XML External Entity (XXE) attacks, showing how insecure XML parsing can be abused to extract sensitive information. Finally, the participants explored metadata server abuse within AWS, learning how improperly secured metadata endpoints can provide access to critical credentials.
Remediation Methods
The retrospective session connected each exploit to its corresponding defense strategy. For network scans, the discussion centered on blocking ICMP pings, restricting port access, and whitelisting trusted IPs. In the case of SQL injection, best practices included the use of ORM frameworks, application-layer validation, and AWS WAF SQL protection rules. For XXE attacks, the remediation involved disabling DTDs, enforcing secure XML parsing, and applying AWS WAF managed rule sets. Finally, to prevent metadata server abuse, the team demonstrated how enabling IMDSv2 on EC2 instances effectively mitigates the risk.
Outcome
By the end of the event, participants had gained practical, first-hand experience of how attackers approach and exploit vulnerable systems. The retrospective reinforced the lessons, bridging the gap between offensive techniques and defensive practices, and equipping attendees with actionable knowledge they could apply in their future engineering work.
Conclusion
Capture the Flag events are far more than simulated exercises—they are immersive, hands-on experiences that bridge the gap between theoretical knowledge and real-world security practice. CTFs equip participants with a first-hand understanding of how attackers think and operate, helping them identify vulnerabilities, anticipate potential exploits, and strengthen both individual and organizational defenses.
By combining realistic environments, customizable challenge levels, and in-depth post-event retrospectives, TrackIt transforms learning into actionable insight. Teams leave not only with enhanced technical skills but also with a stronger culture of security awareness, making them better prepared to safeguard critical systems and data.
About TrackIt
TrackIt is an international AWS cloud consulting, systems integration, and software development firm headquartered in Marina del Rey, CA.
We have built our reputation on helping media companies architect and implement cost-effective, reliable, and scalable Media & Entertainment workflows in the cloud. These include streaming and on-demand video solutions, media asset management, and archiving, incorporating the latest AI technology to build bespoke media solutions tailored to customer requirements.
Cloud-native software development is at the foundation of what we do. We specialize in Application Modernization, Containerization, Infrastructure as Code and event-driven serverless architectures by leveraging the latest AWS services. Along with our Managed Services offerings which provide 24/7 cloud infrastructure maintenance and support, we are able to provide complete solutions for the media industry.

