Security Practices
Security is the foundation of TrackIt’s AWS professional service practice.
Security services are designed around AWS best practices as outlined in the Well-Architected Framework, and CIS Cloud Security Benchmarks.
Cloud Security Solutions
The AWS Security Assessment identifies misconfigurations, vulnerabilities, and security gaps within your AWS environment. By adhering to AWS guidelines and industry best practices, this service provides actionable recommendations to improve your cloud security posture.
Penetration Testing simulates real-world attacks to uncover vulnerabilities that traditional assessments might miss. This hands-on approach ensures organizations can proactively address potential threats, enhancing the resilience of their AWS infrastructure.
AWS Security Assessment
Compare your existing AWS environment against the benchmarks set by the AWS Well-Architected Framework and CIS Cloud Security Benchmarks. Our team of cloud experts will analyze your AWS configurations, applications, and data controls, identifying vulnerabilities, areas for improvement, and strategies to enhance your security posture.TrackIt will deliver a remediation report highlighting areas of strength and weakness, plus recommendations for a more secure AWS cloud.
AWS Account Structure: Ensuring that accounts are isolated appropriately.
Service Control Policies (SCPs): Reviewing and assessing your organization’s permissions and guardrails at the account, organizational unit, and organization level.
Central Control Configurations: Evaluating your current central control configurations.
AWS Tools: Reviewing current AWS tools and identify opportunities to increase automation and improve efficiency.
IAM: Assessing your identity and access management posture including Single-Sign-On (SSO), Multi-Factor Authentication (MFA), external identity federation, credential rotation policies, and password policies.
Detective Controls: Reviewing detective controls such as CloudTrail, GuardDuty, Security Hub, AWS Config, and Trusted Advisor.
Network and Application Security: Assessing network and application security including security groups, NACLs, network firewalls, private links and service endpoints, VPN, WAF, and DDoS mitigation tools.
Monitoring & Log Management: Evaluating your organization’s monitoring and log management processes including CloudWatch log configuration, AWS ElasticSearch, CloudWatch log metric filter, and analysis of S3 logs using GuardDuty and Macie.
Encryption Policies: Reviewing encryption policies including encryption of S3 buckets, EBS volumes, RDS databases, Elasticsearch/OpenSearch, and AWS Certificate Manager.
Security Incident Response Plan: Assessing your organization’s security incident response plan.
Application Architecture: Identifying opportunities to optimize application architecture based on AWS security best practices.
Prowler: Conducting a Prowler (v3 with configuration) scan and review, as well as a cloudsplaining scan and review.

AWS Security Assessment
Learn more about the AWS security assessment process.
Penetration Testing
Recognize and fix security vulnerabilities in your networks and applications.Penetration tests conducted by TrackIt follow the Penetration Testing Execution Standard (PTES) Technical Guidelines, ensuring adherence to best-practices throughout the testing process. Our penetration testing methodology aligns with AWS’s policies and utilizes the latest ethical hacking techniques.
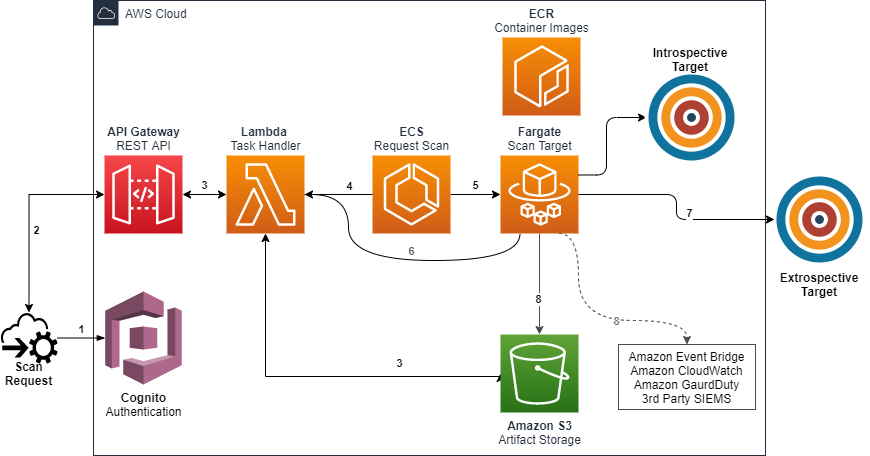
Reconnaissance: Gathering information about the target system, network or application, including IP addresses, domain names, and other publicly available information.
Vulnerability Scanning: Using automated tools to scan for known vulnerabilities in the target system, network, or application.
Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access to the target system, network or application.
Post-exploitation: Performing additional activities after gaining access, such as escalating privileges, pivoting to other systems, or exfiltrating data.
Reporting: Documenting the results of the pen test, including vulnerabilities found, the severity of the vulnerabilities, and recommendations for remediation.
Remediation validation: Verifying that remediation activities have effectively addressed identified vulnerabilities.
Re-testing: Repeating the pen test to ensure that all vulnerabilities have been successfully remediated.

Penetration Testing
Learn more about the Penetration Testing process.
FAQs
What AWS Security Services can TrackIt help me implement?
TrackIt can help implement AWS security services such as:
- AWS WAF (Web Application Firewall): Protects web applications from common exploits and malicious traffic.
- AWS Shield: Defends against Distributed Denial of Service (DDoS) attacks.
- AWS GuardDuty: Provides threat detection and continuous monitoring for malicious activity.
- AWS Security Hub: Centralizes security alerts and compliance checks across AWS accounts.
- Amazon Inspector: Automates security assessments to identify vulnerabilities in EC2 instances and container workloads.
- AWS CloudTrail: Tracks user activity and API usage for governance, compliance, and risk auditing.
